
8 Kubernetes Security tips for cloud engineers
For nearly 40% of DevOps and engineers, Kubernetes security isn't taken seriously enough. So what steps can be taken to protect your clusters? Here are some useful tips...

Kubernetes 1.28, code-named 'Planternetes’, is the latest minor release of the popular container orchestration platform.
This is a significant release that includes 40+ new features or improvements, with a focus on security and performance. This article will focus on 2 enhancements that caught our eye.
Security is a paramount concern for Kubernetes administrators, and rightly so. The evolving landscape of digital threats poses risks that must be proactively addressed.
Imagine the vulnerabilities, from unauthorized access and resource overutilization to potential network breaches and compromised container images. The consequences could be devastating, resulting in data breaches, service disruptions, and reputational damage.
To fortify your Kubernetes environment, it's crucial to adopt robust security measures. In the latest iteration of Kubernetes, version 1.28, significant strides have been made in enhancing security features. Notably, Validating Admission Policy has graduated to the beta stage, solidifying its position as a fundamental tool in your security arsenal.
Let's delve into why this advancement is so noteworthy.
At its core, the Validating Admission Policy feature empowers administrators to define and enforce an array of security policies with finesse. This spans essential aspects such as access control, resource quotas, network security, and the integrity of container images.
What sets this feature apart is its foundation on the Common Expression Language (CEL). By harnessing CEL's capabilities, administrators can articulate policies that evaluate conditions, perform intricate calculations, and manipulate data with precision. The versatility of CEL, already employed in Kubernetes for a range of purposes including Custom Resource Definitions (CRDs), lends itself seamlessly to crafting these policies.
Contrast this with the established tools like Kyverno or Gatekeeper (OPA). Unlike these tools, the Policy as Code admission controller doesn't necessitate external program calls. This inherent efficiency translates to quicker policy enforcement without the latency associated with external dependencies. It's akin to having a vigilant security guard stationed directly at your entrance instead of awaiting instructions from a distant command center.
The impact of Validating Admission Policies reverberates across your entire Kubernetes cluster. This feature supersedes service deployment, ensuring that policy adherence is a non-negotiable prerequisite before any deployment takes place.
Care to give it a try? Datadog has thoughtfully provided a sample policy that demonstrates its potential. This example showcases how you can prevent the execution of privileged containers within the default Kubernetes namespace.
Policy as Code in CEL for admission control is a new era of proactive and finely-tuned security. By enabling administrators to define, evaluate, and enforce policies in a language as powerful as CEL, Kubernetes takes a significant stride towards offering administrators a comprehensive suite of tools to protect their environments.
Policy as Code alpha feature gate has been supported by Scaleway since Kubernetes 1.26 and we are excited to see what our users will do with it moving forward.
As auxiliary containers sitting along your main workloads, sidecar containers can perform a bunch of tasks for a variety of purposes:
In the past, sidecar containers were difficult to implement, requiring the use of webhooks or IaC approaches. With version 1.28, Sidecar containers are now first-class Kubernetes citizens!
The alpha feature gate brings lightweight containers that run alongside application containers, in a pod. With this feature, you can set the restartPolicy field to Always on an init container, and Kubernetes will treat it as a sidecar container.
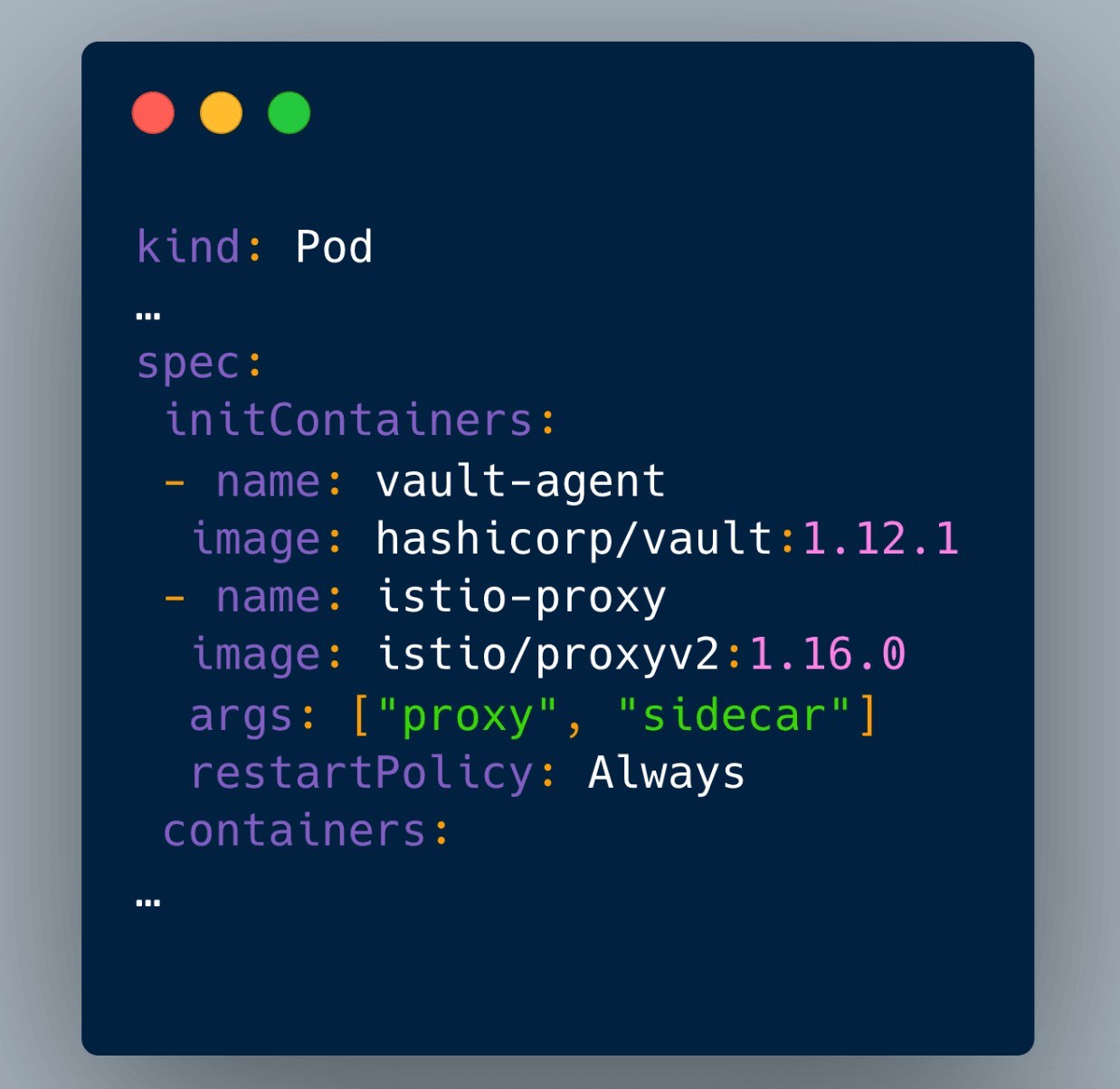
This is a welcome addition to the Kubernetes ecosystem, and it will make it easier for developers to build more reliable and secure applications.
More sidecar details and examples can be found in this great blogpost.
Kubernetes 1.28 also makes upgrades more reliable and reduces downtime with UVIP, Kube-proxy improvements, and proxy terminating endpoints. Furthermore, Kubernetes 1.28 removes no APIs, so you can upgrade to it without worrying about breaking your applications!
We strongly recommend users keep their Kubernetes clusters up-to-date with the latest available minor versions of Kubernetes and the latest patches. Kubernetes 1.28 is now available via the Scaleway console. Scaleway offers managed Kubernetes services, namely Kapsule and Kosmos for multi cloud, and supports a wide range of Kubernetes versions (up to 7 minor versions as of writing!).
The Validating Admission Policy beta feature gate and SidecarContainers alpha feature gate introduced above are enabled for all Kapsule and Kosmos clusters on v1.28, Kubernetes' latest version.

For nearly 40% of DevOps and engineers, Kubernetes security isn't taken seriously enough. So what steps can be taken to protect your clusters? Here are some useful tips...
To understand why Kubernetes and containerized deployment is so useful for nowadays workloads, let us go back in time and have a view on how deployment has evolved

We will be using a Kubernetes Kosmos cluster, and deep-diving into specific multi-cloud Kubernetes concepts