Europe's cyberattack landscape in 2024
In 2024, Europe saw an explosion in cyberattacks targeting web applications and information systems. According to ENISA (European Union Agency for Cybersecurity), the most frequent attacks concerned service availability (DDoS attacks), ransomware and breaches of sensitive data. This upsurge is all the more worrying as cybercriminals are massively targeting small and medium-sized enterprises (SMEs), which are often less prepared for these threats.
Companies most affected
The Hiscox 2024 report reveals that 67% of European companies have suffered at least one cyber attack this year, with a marked increase in attacks against SMEs and very small businesses (VSEs). These structures often have limited resources to defend themselves, making them more vulnerable to cybercriminals.
Compliance challenges in Europe
Faced with this intensification of threats, the European Union has strengthened its regulatory arsenal. The NIS2 directive, which came into force in 2024, now imposes strict security and incident reporting obligations on businesses and digital service providers. The Cyber Resilience Act also reinforces companies' responsibility to secure their digital products and services.
Secure and optimize with WAF and Caching
To meet these challenges, two complementary solutions exist: Web Application Firewall (WAF) and Caching via its Edge services. These tools protect web applications against cyber-attacks, while enhancing their performance.
Web Application Firewall (WAF) : One of the first line of defense
WAF acts as a shield between users and web applications. It filters and monitors HTTP/HTTPS traffic to block attacks such as: SQL injections (SQLi), cross-site scripting (XSS).
WAFs offer sensitivity levels, also known as “paranoia levels”. Think of it as a slider that you can adjust according to the level of vigilance you wish to apply to the protection of your web application.
- Level 1: Ideal for a relaxed approach, this level lets more traffic through while blocking obvious attacks. It's perfect if you want to avoid false positives (situations where legitimate requests are blocked by mistake).
- Level 2: A good compromise between vigilance and flexibility. It filters out common threats while allowing the majority of legitimate interactions to pass through unhindered.
- Level 3: Here, the WAF becomes much stricter, blocking anything that might resemble a threat, even indirectly. It's the right level for sensitive environments where security is more important than permissiveness.
- Level 4: This level is designed for ultra-sensitive applications, such as those in the banking or healthcare sectors. The WAF scrutinizes every request with extreme care, letting nothing through that could represent even the slightest potential threat.
With these sensitivity levels, WAF easily adapts to your needs, whether you want to maintain a smooth user experience or completely lock down your web application against threats.
WAF also offers :
- Flexible modes, including log only to check the impact WAF may have on traffic before going into production.
- Exclusion rules
- As a monitoring tool, companies benefit from real-time visibility of their security.
Coping with the most common attacks
Faced with constantly evolving cyber threats, companies today need not only to optimize the performance of their applications, but also to protect them against the most sophisticated attacks. This is where managed WAFs come in. Designed to block the vulnerabilities identified by the OWASP Top 10, these solutions are becoming indispensable in an increasingly hostile digital environment.
The OWASP Top 10 represents the main web application security vulnerabilities that a managed WAF can effectively address:
-Broken Access Control: Prevents unauthorized users from accessing sensitive data or functionality
-Cryptographic Failures: Protect sensitive data in transit or at rest with secure encryption mechanisms
-Injection: Blocks malicious requests such as SQL or LDAP injections
-Insecure Design: Prevents attacks by detecting risky design patterns
-Security Misconfiguration: Reduces errors linked to misaligned or obsolete configurations
-Vulnerable and Outdated Components: Blocks threats exploited via insecure libraries or frameworks
-Identification and Authentication Failures: protects authentication mechanisms against attacks such as session theft
-Software and Data Integrity Failures: Prevents malicious manipulation of data or software
-Security Logging and Monitoring Failures: Provides real-time visibility of threats via logs and alerts
-Server-Side Request Forgery: Intercepts requests diverted to unauthorized resources
Unlike traditional solutions requiring complex management, a managed WAF offers turnkey protection against these threats. It automatically manages configuration, rule updates and even event logging. The result? Companies benefit from robust defense without having to mobilize internal resources. With a managed WAF, you get not only optimized performance thanks to integration with CDNs, but also enhanced security that protects your data and users against the most common threats. For SMEs and large enterprises alike, it's a solution that combines simplicity, efficiency and peace of mind.
Often considered a simple performance optimization tool, caching also plays an interesting role in security. By temporarily storing static content on distributed cache servers, it helps to mitigate DDoS attacks by effectively absorbing spikes in malicious traffic. This intelligent distribution of traffic across a network of caching nodes considerably reduces the impact of attacks, protecting the main infrastructure and ensuring continuity of service.
The WAF and Caching combo, an ideal solution for SMEs
Small and medium-sized businesses, which are at greater risk due to limited resources, can considerably enhance their security by combining WAF and Caching.
A winning duo against cyberthreats
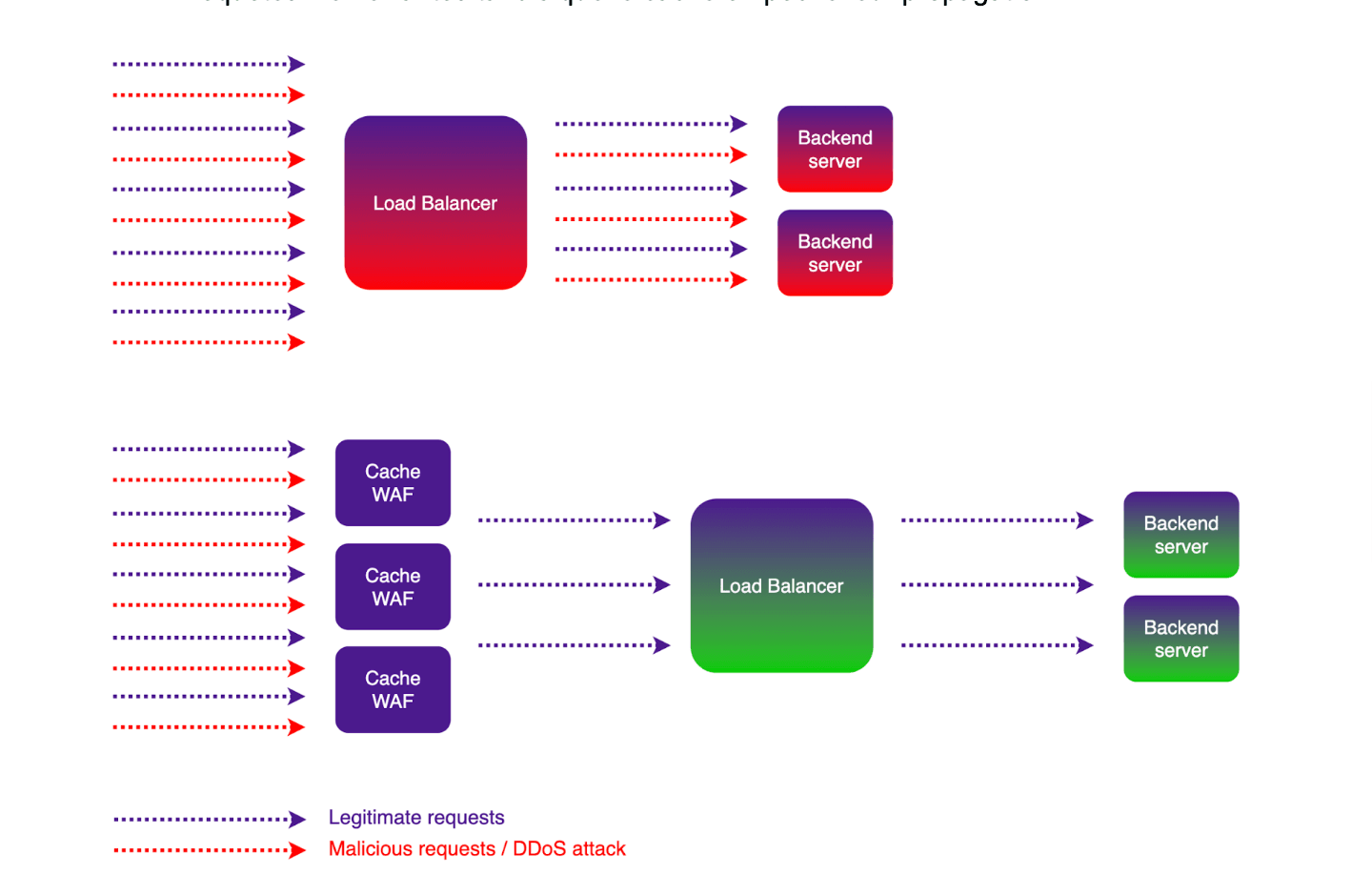
- Reduced attack surface: Caching limits direct access to origin servers, reducing entry points for cybercriminals.
- Protection against DDoS attacks: By absorbing massive traffic, caching prevents server saturation.
- Limitation of OWASP Top 10 and other attacks (XSS, etc.): WAF filters out malicious requests, while caching prevents their propagation
Conclusion
By combining WAF and Caching solutions, companies benefit from dual protection: enhanced security and optimized performance. This proactive approach not only enables compliance with new European regulations, but also ensures business continuity in the face of growing cyber threats.
Protect your business today with Scaleway. Anticipate tomorrow's threats to ensure your long-term survival.