The fundamentals of anti-DDoS protection

DDoS Protection: Key Principles and Mechanisms
Distributed Denial-of-Service (DDoS) attacks are attempts to disrupt the activity of a service, server, or network by continuously flooding it with requests. The origin of these requests is a network of systems purposefully infected by malicious software. This botnet network acts in tandem to flood the victim’s bandwidth or compute resources. The distributed nature of the flood makes it harder to stop the attack, as the threat is coming from several sources at once.
According to the MIT Technology Review, the first recorded attack dates back to 1999, when a malicious script caused a network of 114 computers to send superfluous data packets to a computer at the University of Minnesota, rendering it inaccessible for two days. In the following month, this practice began to spread, incurring attacks on major websites of the time such as CNN, Amazon, and Yahoo.
In the following 20 years, this type of cyberattack became a popular tactic among hacktivists and businesses targeting competitors, as it proved to be a powerful weapon of activity disruption and resulted in important financial losses.
According to Cloudflare[1], an exponential increase in the number of DDoS attacks and their dimension, was observed from 2010 to 2024. At the beginning of the 2010s, the total transferred data in the largest known attacks was measured in Gbps, whereas now the data is measured in Tbps, meaning that the space it takes up has increased by 1000 times (Figure 1). In only the last six months, NETSCOUT[2] observed a 12,8% increase in the number of attacks compared to the last semester of 2023.
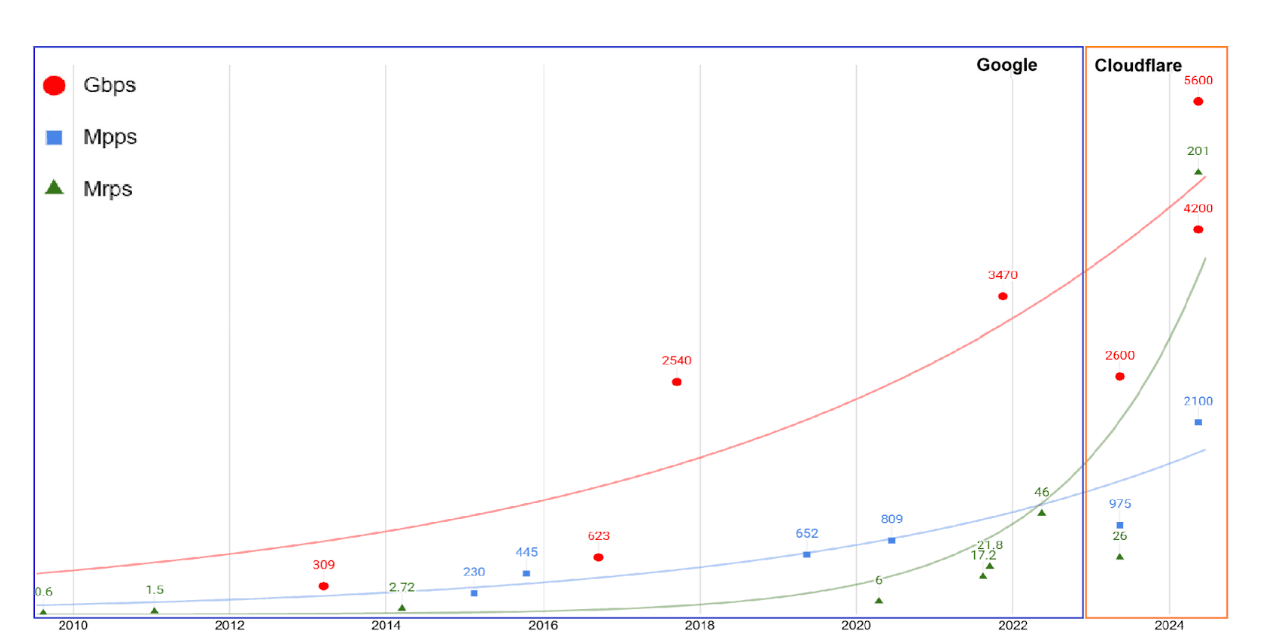
These numbers help us understand the importance of investing in protection and security measures against DDoS attacks. Since the sources of the attack are distributed, however, it is hard to act on the attack once it has already started. This is why prevention is key when dealing with DDos.
But before knowing how to prevent these attacks, we need to understand how they work.
Types of DDoS Attacks
There are 3 types of DDoS attacks: Volumetric, Protocol, and Application-Layer. These types are defined according to which layer of the network connection[3] they attack and the distributed method used to render the victim's system inoperable.
Volumetric attacks
Volumetric attacks flood the victim’s network capacity with excessive traffic, causing bottlenecks in bandwidth and throughput. Large amounts of data are sent to the target by a botnet, a network of internet-connected devices compromised by malware that is, as a consequence, under the control of the attacker. Since many large packets are sent at once, the system cannot process all requests at once, resulting in packets being buffered and then dropped.
The goal is to create enough congestion that all the available network capacity is consumed, render the system unavailable to receive legitimate traffic, and make it vulnerable to other threats.
Protocol attacks
Protocol attacks benefit from protocol weaknesses in the transport and network layers of the network connection framework. These layers correspond to layers 3 and 4 of the OSI model.
In this type, service disruption is caused by the exhaustion of server and/or network resources. Usually, the attacker will make requests to the victim’s server that will not behave according to the established protocol, causing the server to allocate resources and memory to handle malicious requests that have no intention of being completed.
A common method used is a SYN flood, in which attackers send numerous SYN requests to a server but do not complete the expected TCP handshake with the ACK response. While the handshake is not completed, the server will keep the incomplete sessions running. Many concurrent incomplete sessions may render the system inoperable.
Application-layer attacks
This type of DDoS attack targets layer 7 of the OSI model : the application layer. This is where web services are accessible to clients, and where HTTP requests are received and responses delivered. Behind this, the server infrastructure is activated, implicating memory and computing power to query databases and load files, for example. In cloud-native applications, such requests may trigger autoscaling features.
A high volume of requests can incur high costs. Meanwhile, for the attacker, a simple HTTP request requires little effort and cost.
Since the application layer is the last of the OSI model and the first the client comes into contact with, the network footprint of the attack is smaller. This, paired with the difficulty in distinguishing a legitimate request from a malicious one, can render this attack type one of the hardest to identify and mitigate.
Multi-vector attacks
The three types of attacks described above can also be combined in what is called a multi-vector attack.
Multi-vector attacks have been observed since 2010[4]. As a reflection of the advancement of DDoS technologies, they have become more popular with the proliferation of IoT devices and cheap, streamlined DDoS attack tools.
The combination of all three techniques makes an already complex identification and mitigation process even more complicated to deal with.
Why your infrastructure needs protection
As mentioned before, the main and most immediate impact of DDoS attacks on a system is rendering services unavailable or inoperable. Different parts of a service’s infrastructure may depend on and/or be controlled by the server being attacked, so the consequences may go further than just impacting one single server.
Service downtime can cause customer frustration, impacting the business’ reputation and incurring potential financial losses.
Furthermore, when a system is overwhelmed, it becomes vulnerable to other cyberattacks. While the server is busy handling the load of the DDoS attack, it will certainly have a harder time mitigating a second attack.
Protection solutions for your infrastructure
When it comes to DDoS attacks, prevention is key.
Implementing DDoS identification mechanisms is equally important, but when faced with a multi-vector attack, for example, you’ll likely not know where the threats are coming from right away. It’s easy to conflate normal with malicious traffic, especially in situations where large volumes are expected.
Depending on your infrastructure setup, you can implement protection for your services by combining several of the following techniques:
Traffic filtering and rate limiting
When deciding which prevention methods to apply, consider that the less you expose your server’s network, the better. It is important to reduce the surface of exposure by restricting traffic to specific parts of the infrastructure, avoiding communication that uses outdated applications, ports, or protocols. If you know where the attack is coming from, a simple action is to block the IPs carrying out the threat through IP blocklisting.
Companies dedicated to cyberattack mitigation can also offer intelligent traffic filtering, where advanced algorithms and behavioral analytics are used to differentiate between legitimate user activity and malicious traffic.
You can also limit the number of requests per second a server can process from a single source with rate limiting.
Reinforcing your network infrastructure
Tools like firewalls and Intrusion Prevention Systems (IPS) help you filter out malicious traffic before it reaches systems by blocking suspicious activity at the network level.
You can also set up a load balancer to distribute incoming traffic across multiple servers and prevent any single server from being overwhelmed during an attack, or only in case of periods of high demand.
To protect your websites, you can deploy security headers to prevent exploits like cross-site scripting (XSS) and ensure SSL/TLS encryption to protect data in transit.
Web Application Firewalls (WAF) are another method commonly used to filter and monitor HTTP traffic between web applications and users. Watch this space for Scaleway's upcoming WAF feature, currently being integrated into our Edge services product.
Behavioral analysis and anomaly detection
Monitoring and analyzing network logs is a crucial part of any anti-DDoS prevention system. To identify any threats, you must first know what your regular network activity looks like. This is why tools like intrusion detection systems, security information, and event management platforms must be configured as soon as you set up your infrastructure. The sooner monitoring mechanisms are used and the more frequently they are checked, the easier it is to identify anomalies should they occur.
At Scaleway, you can use Cockpit to monitor your cloud resources. Cockpit stores metrics, logs, and traces and provides a dedicated dashboarding system on Grafana for easy visualization. Different metrics are available for different resource types, with metrics for network traffic being available for many, enabling you to monitor connections over the public interface.
Redundancy and failover systems
Even though the ultimate goal is avoiding attacks from happening altogether, it is important to have a plan B in case your service is compromised.
It is a good practice to deploy backup servers and alternate routing paths that take over automatically if the primary system is compromised. These redundancy and failover systems ensure the continuity of your service by rerouting legitimate traffic and reducing downtime.
Cloud-based DDoS mitigation
You can employ cloud-based services, such as Content Delivery Networks (CDNs), to implement a scalable defense strategy.
CDNs distribute incoming traffic across a distributed global network of servers. This ensures that malicious traffic is absorbed by the CDN and filtered before it reaches the target, avoiding overloads. Additionally, CDNs can cache the content of a web service and handle legitimate traffic while the malicious data is being mitigated, ensuring continuous activity.
Managed DDoS mitigation services
You can implement and manage all the techniques above, but you can also outsource DDoS mitigation services to companies dedicated to computing security solutions.
If you lack the in-house resources to implement defense against large-scale or sophisticated attacks, managed solutions can help unburden you of not only the setup but also the monitoring of your network infrastructure protection. Managed solutions often include 24/7 monitoring, traffic analysis, intelligent traffic filtering, and rapid mitigation strategies.
Best Practices for Long-Lasting Protection
Once one or more of these methods are implemented and managed, you must also make sure that they are maintained and remain effective in the long run.
Carrying out regular security audits is recommended for identifying vulnerabilities in your infrastructure, such as outdated software, misconfigurations, or exposed endpoints, and addressing them proactively.
Training your staff to recognize and respond to a threat can also significantly reduce the risk of breaches caused by social engineering or negligence.
Staying up-to-date on emerging attack technologies, trends, and tools, as well as researching new protection methods and integrating them will help you anticipate and prepare for potential risks.
Anti-DDoS at Scaleway
Scaleway relies on managed mitigation services to stop and avoid attacks. We leverage Netscout’s anti-DDoS solution, Arbor Protection, to efficiently safeguard our entire infrastructure, from internal services to all the solutions we offer to our clients.
If you have a dedicated Dedibox server, you can subscribe to personalized anti-DDoS mitigation managed by our support team.
Scaleway offers three anti-DDoS plans for Dedibox servers:
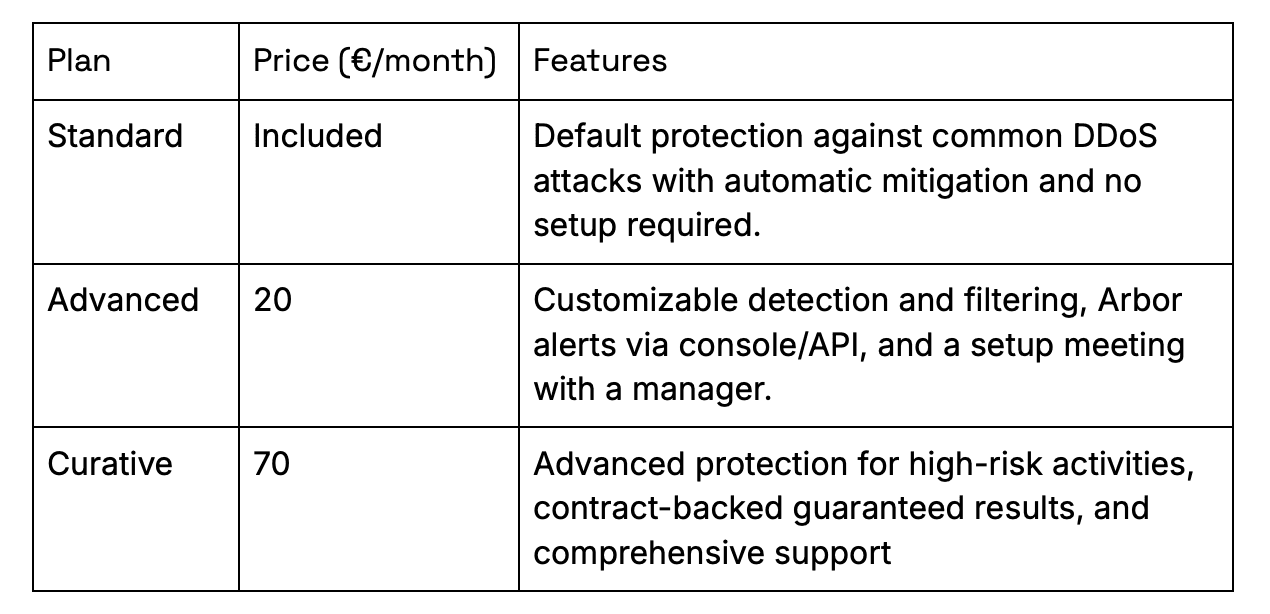
Learn more at Scaleway DDoS Protection.
Sources
1 - Bigger and badder: how DDoS attack sizes have evolved over the last decade - Cloudflare Blogpost
2 - NETSCOUT DDoS Threat Intelligence Report / Issue 13: Findings from 1H 2024 - Global Highlights
3 - OSI Model Specifications - ISO/IEC 7498-1:1994
4 - How to Analyze and Reduce the Risk of DDoS Attacks - Netscout Whitepaper