Manage Zigbee connected devices with Scaleway IoT Hub
Privacy and security concerns should be at the forefront of any deployment of connected devices used to monitor or automate actions in our physical environment. Zigbee is a recognized protocol to create a mesh network of sensors and actuators in houses and apartments. However, a proprietary gateway is often used to send commands and receive information to and from this network. It results in a trade-off in control over the security level and the automation and monitoring capabilities. This tutorial aims to set the foundation of a fully configurable solution based on the open source zigbee2mqtt software and the IoT Hub managed service from Scaleway.
Scaleway IoT Hub is a resilient and MQTT message broker with export capabilities. The use of a message broker will enable us to increase the interoperability of the solution.
Creating an IoT Hub
- Create an IoT Hub (shared plan) for testing purposes, following the available documentation. Dedicated and High availability plans remain recommended for more critical workloads.
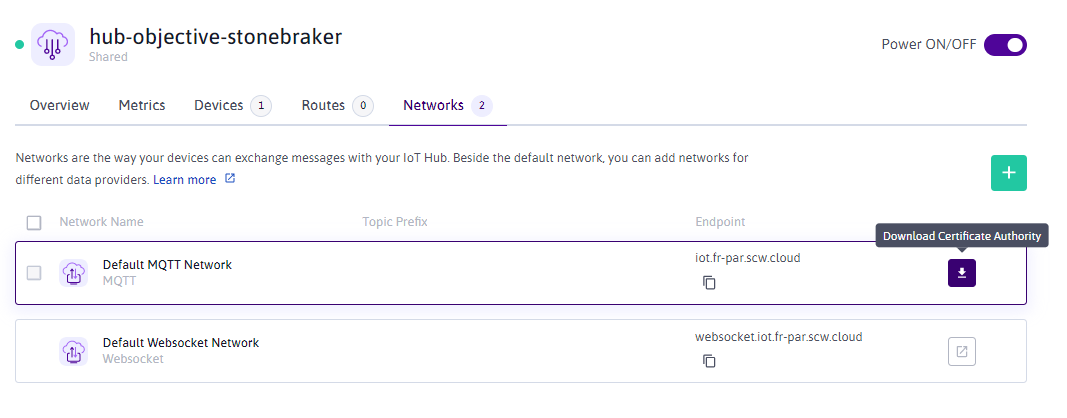
- Add a new device to the Hub, with the option "Deny insecure connection" selected. You need to download download icon the device certificate and device private key, as well as the Device ID.
- Download download icon the certificate used to secure the MQTT endpoint in the Networks tabs.
Installation and configuration of Zigbee2mqtt
Zigbee2mqtt can be installed on a single board computer such as a Raspberry Pi and you should follow first the installation instructions. This tutorial assumes that you have a proper installation of Zigbee2mqtt and that your network of connected devices is configured.
Configuration of MQTT
Zigbee2MQTT is configured using YAML based configuration.yaml file. Modify this configuration file to include the following MQTT settings.
# Required: MQTT settings
mqtt:
server: mqtts://iot.fr-par.scw.cloud:8883 # mqtts endpoint
base_topic: zigbee2mqtt
ca: /etc/ssl/mqtt-ca.crt # Certificate Authority
key: /etc/ssl/mqtt-client.key # Device private key
cert: /etc/ssl/mqtt-client.crt # Device certificate
client_id: <Device_ID>
keepalive: 60
version: 4
force_disable_retain: trueAs soon as the configuration is done, you will see some metrics on the Scaleway console.
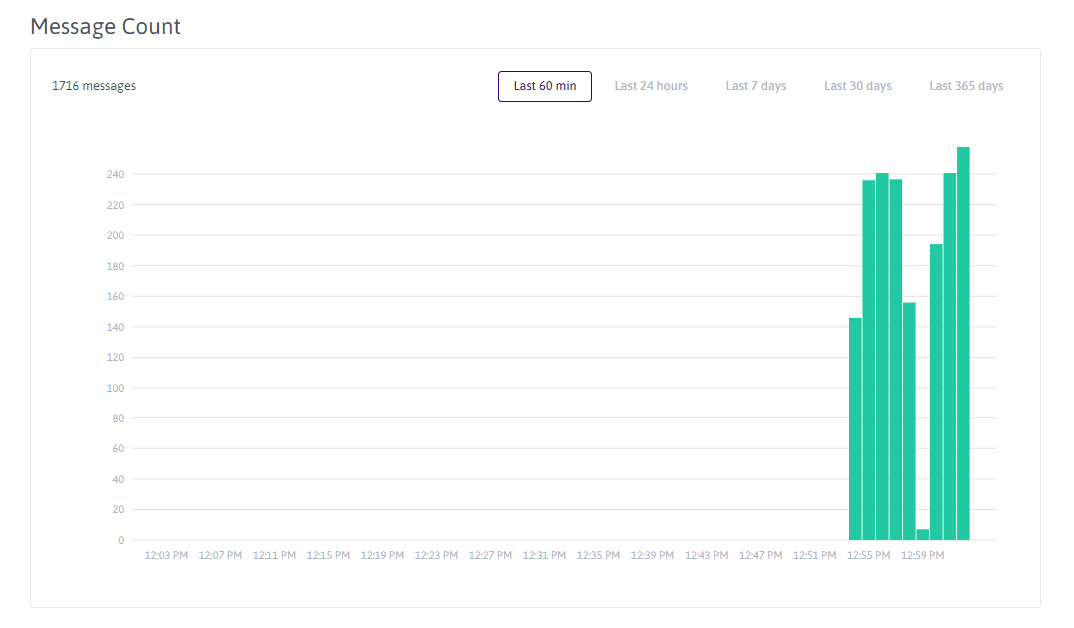
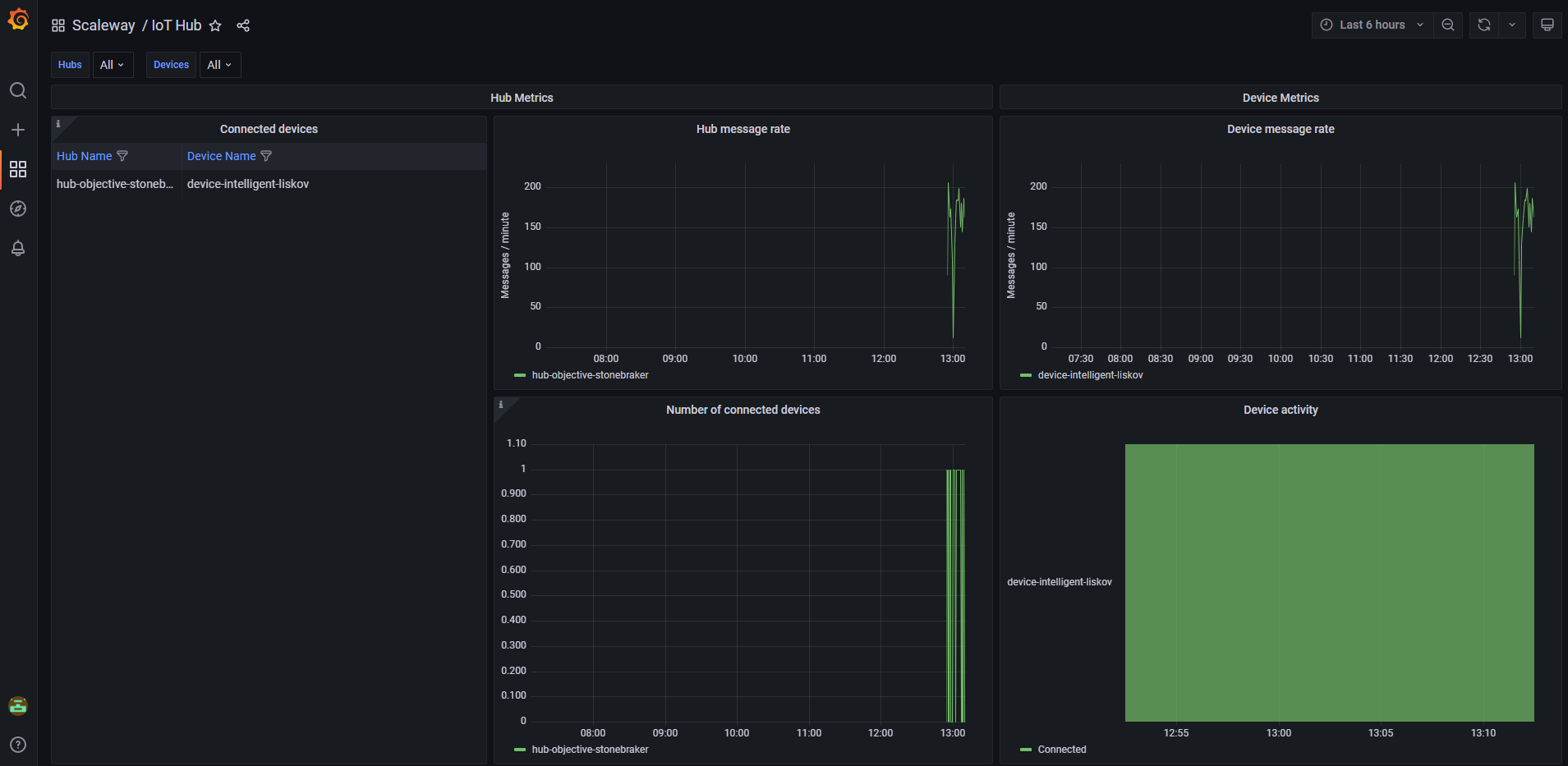
Thanks to Scaleway built-in integration, similar metrics to monitor the performance of your IoT Hub are also available on your Scaleway Observability dashboard.
Visit our Help Center and find the answers to your most frequent questions.
Visit Help Center