Secret Manager - Concepts
Disabling a version
Disabling a version is the action of temporarily revoking access to the data contained within a specific version. This prevents any users and applications from accessing your data.
Refer to the How to manage a version documentation page for more information.
Enabling a version
Enabling a version is the action of making the data contained within the version accessible for retrieval by authorized users and applications. This allows you to manage access to your data and control which versions are accessible, at any time.
Refer to the How to manage a version documentation page for more information.
Ephemerality properties
When applying an ephemeral policy to your secret, you must define at least one ephemerality property:
- Single access: allows you to set your secret versions to expire after one single access.
- Time to Live: allows you to set a time frame of up to one year, during which your secret versions are valid and accessible.
Ephemeral policy
An ephemeral policy is a statement that defines the lifetime of a secret and its versions, using either the Single access or the Time to Live ephemerality properties. The ephemeral policy also allows you to decide whether to disable or delete your secret's versions, once the versions have expired.
Ephemeral secret
An ephemeral secret is a secret that has a limited lifetime, enforced by an ephemeral policy. All the secret's versions automatically inherit their settings from those of the current ephemeral policy.
Path
A path refers to the directory structure to access your secrets and their versions. Each path is prefixed with a slash.
For example, if you create a secret my-secret within the path /my-path, your secret can be accessed at the /my-path/my-secret path.
PEM
A PEM or Privacy Enhanced Mail file is a security certificate file used to establish a secure communication channel between a web server and a browser. It is encoded in Base64 and may contain a private key, a server certificate and/or a combination of other certificates.
Region
A region is the geographical area in which your secrets, and versions are stored and run. They are duplicated on all Availability Zones of the selected region (Paris, Amsterdam, or Warsaw).
Secret Manager allows you to select your resources by region. This allows you to better sort through your resources, if you have created them in different regions but with the same name, for example.
Secret
Secrets are logical containers made up of zero or more immutable versions, that hold sensitive data. Upon creation, you can choose between 6 secret types. The default secret type is the opaque one.
The secret versions must be of the same type as the secret.
Secret Manager
Secret Manager is a solution that provides a centralized location where your secrets can be stored and accessed. Its primary purpose is to securely store secrets, thus eliminating the need for developers to hard code sensitive information in applications or configuration files.
With Secret Manager, you can also share sensitive data such as passwords, API keys, and certificates.
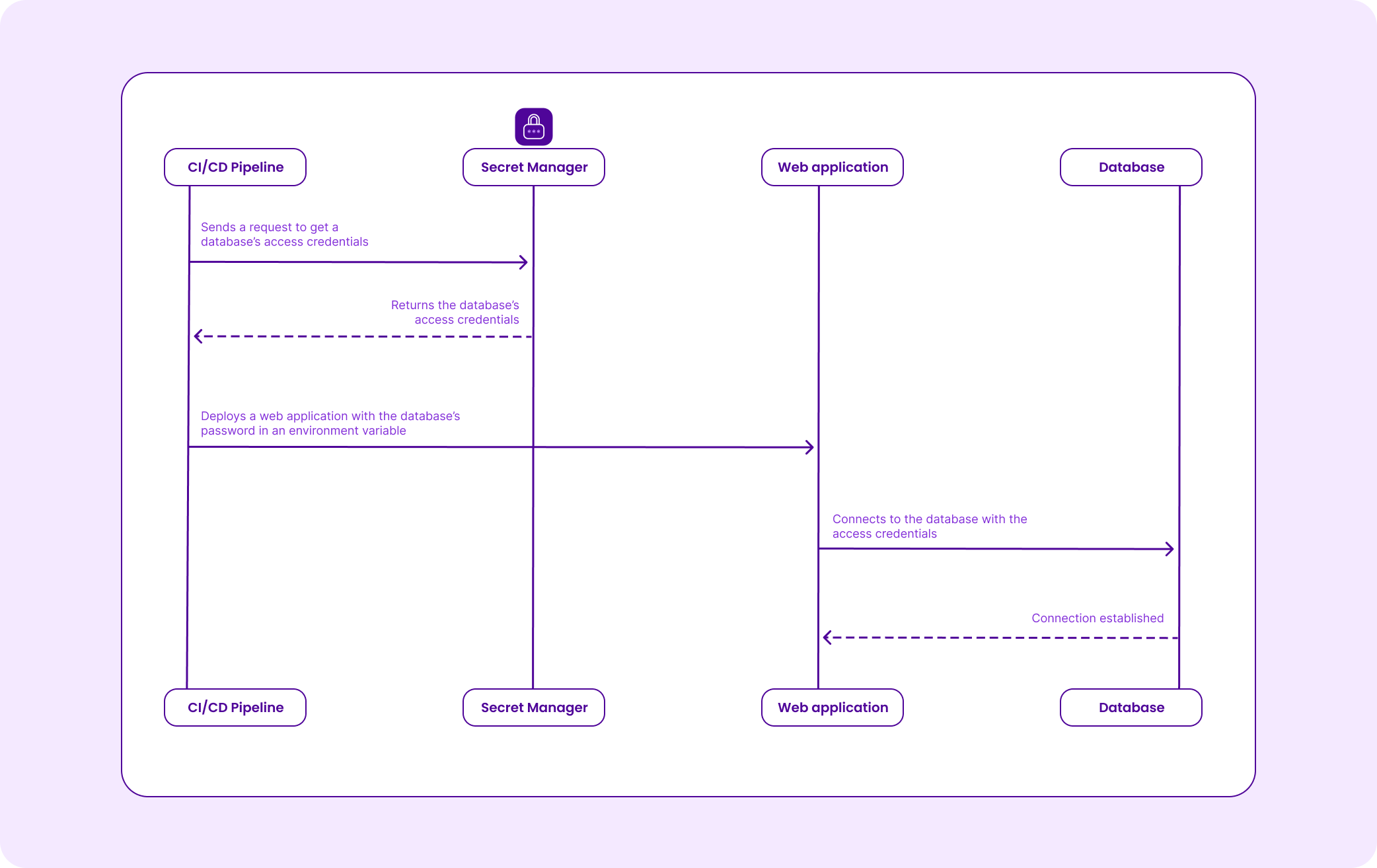
Scaleway's Secret Manager can be managed using APIs and the Scaleway CLI, which allow authorized applications or services to retrieve secrets securely. This enables you to automate a deployment by fetching your passwords stored on Secret Manager through the API, and storing them in your environment variables, which will then be used by your application.
Secret protection
Secret protection is a feature that prevents the deletion of your secrets. Users holding the SecretManagerFullAccess, SecretManagerSecretWrite, and AllProductsFullAccess permission sets can enable it, ensuring that although your secrets can be accessed and modified, they remain impossible to delete.
This ensures the protection of critical information against accidental deletion while maintaining secret management flexibility.
Secret types
Secret types refer to the different kinds of sensitive data you can store with Secret Manager. Using secret types guarantees that all mandatory fields are present, facilitates the application of specific policies, and enhances integration with other products. Refer to the Understanding secret types documentation page for more information on available secret types
Upon secret creation, you must choose a secret type that will also be applied to the secret version. All the secret's subsequent versions must be of the same type.
Scheduled deletion
Scheduled deletion lets you mark a secret and its versions for deletion ahead of time. Instead of immediate deletion, the secret enters a 7-day pending deletion period, during which you can still recover it.
During this time, you can read secret versions but cannot edit, access, or delete them. After the retention period, the secret and all its versions are permanently deleted. You can also schedule a secret version for deletion without impacting the secret associated with the version.
Recovering deleted secrets is billed €0.01 per version associated with the secret.
Tag
Tags allow you to organize your secrets. This gives you the possibility of sorting and filtering your secrets in any organizational pattern of your choice, which in turn helps you arrange, control, and monitor your secrets.
Version
Versions store the data contained in your secret (API keys, passwords, or certificates). Versions can be enabled or disabled depending on your usage. Versions must be of the same type as the secret they belong to.
Refer to the How to add a version documentation page for more information.