Understanding Network ACLs
Every VPC has a Network Access Control List (NACL). This list is composed of stateless rules to control the flow of traffic between the Private Networks of the VPC. By default, at first, the list contains no rules, and therefore traffic is allowed to flow unrestrictedly. You can add rules to restrict traffic flow according to your requirements.
This document sets out general information and best practices about Scaleway VPC NACLs.
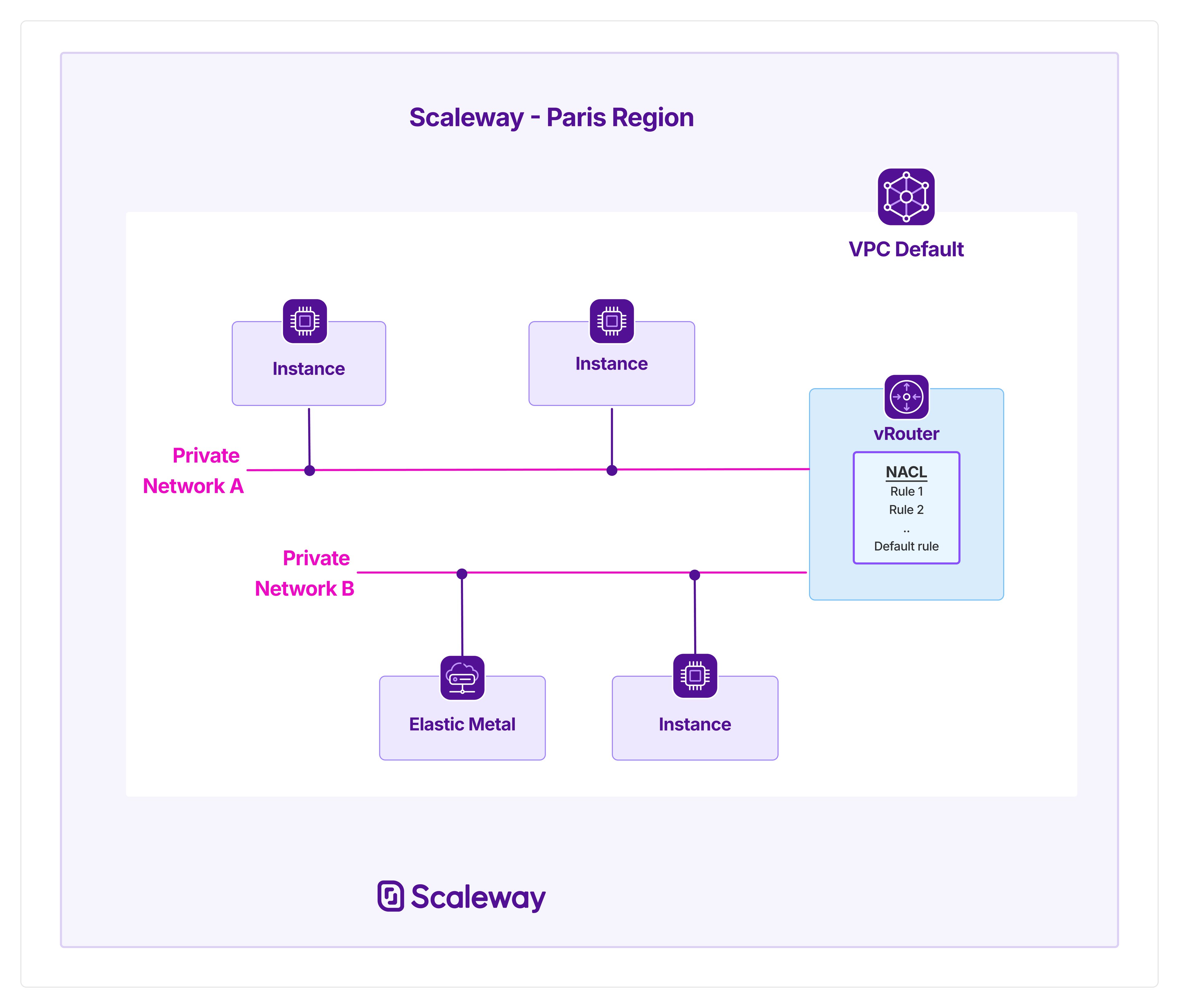
Network ACL overview
Every Scaleway VPC has a Network ACL. In its initial state, it contains no rules. Thanks to managed routing, which automatically routes traffic between Private Networks, traffic is freely routed between the Private Networks of the VPC.
When you start adding rules to your NACL, traffic flow is restricted between certain sources and destinations within the VPC, according to the rules you set. A default rule is added to the NACL, which dictates the action to take on traffic that does not match any rules in the list: it can either be allowed or denied.
NACL rules are stateless, meaning that the state of connections is not tracked, and return traffic is not automatically allowed just because the outbound request was allowed. Explicit rules are required for each direction of traffic.
NACLs only control traffic as it enters or exits the Private Network(s) of a VPC. They do not:
- Filter traffic between resources attached to the same Private Network
- Filter traffic from/to the public internet (for this, use security groups for Instances, or equivalent features for other resource types).
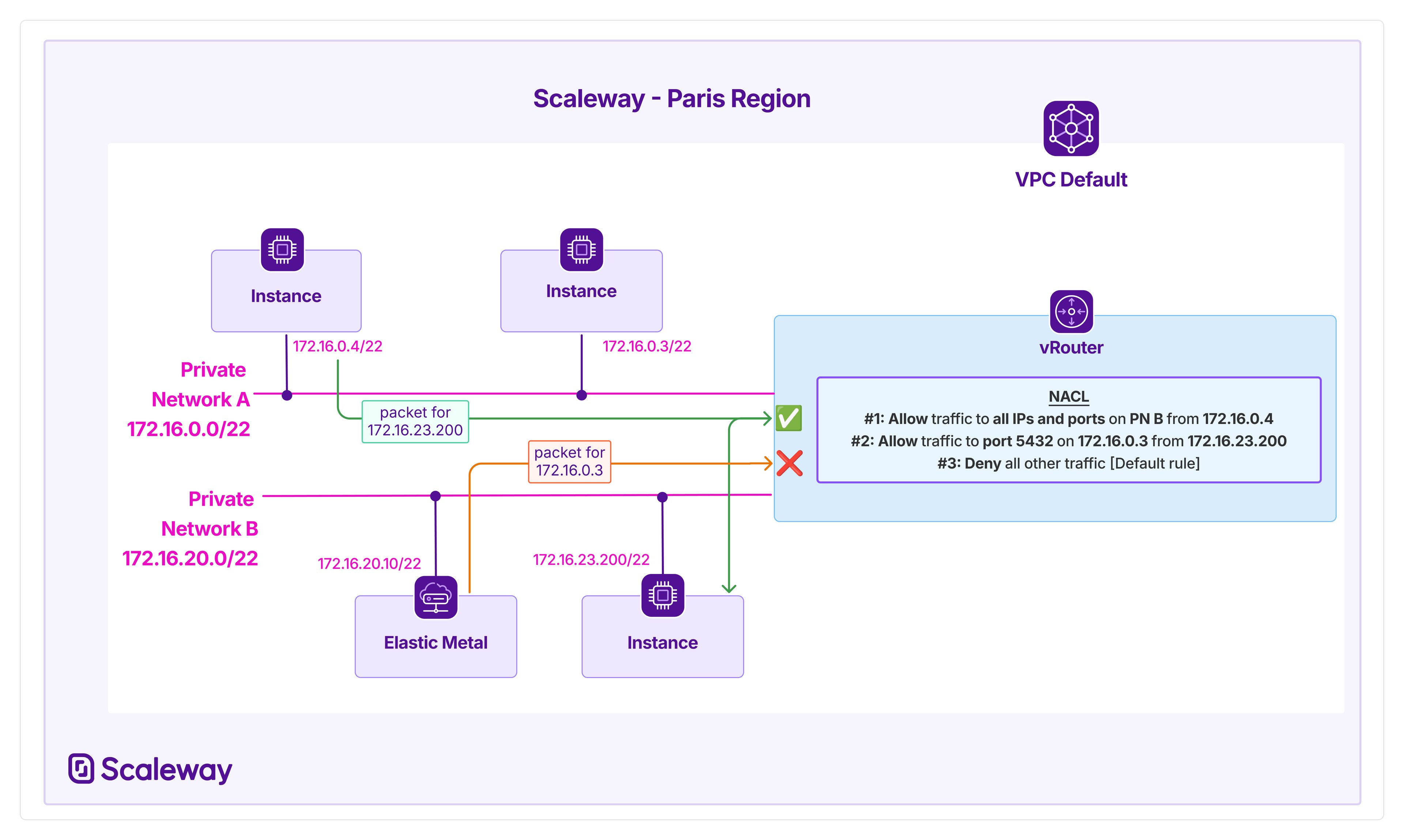
The diagram below shows how a NACL allows an Instance on Private Network A to send a packet to an Instance on Private Network B.
However, an Instance on Private Network B is blocked from sending a packet to an Instance on Private Network A, because no specific rules allow it to do so, and the default rule is set to Deny.
NACL rule configuration
When defining a NACL rule, you must enter the following settings:
-
IP version: Either IPv4 or IPv6. The rule will apply only to traffic matching this IP version, meaning that in effect, each VPC has two NACLs: one for IPv4 and one for IPv6. If you want to create an equivalent rule for the other IP version, you must do so separately.
-
Protocol: Either
TCP,UDP, orICMP. The rule will apply only to traffic matching this protocol. Alternatively, you can choose to apply it to traffic matching any protocol. -
Source and destination: The rule will apply to traffic originating from this source and being sent to this destination. For both, enter an IP range in CIDR format, and a port or port range. Alternatively, you can opt for the rule to apply to all IPs and/or all ports.
-
Action: The NACL will either Allow (accept) or Deny (drop) traffic that matches the rule.
Rule priority and application
The Network Access Control List should be read from top to bottom. Rules closer to the top of the list are applied first. If traffic matches a rule for an Allow or Deny action, the action is applied immediately. That traffic is not then subject to any further filtering or any further actions by any rules that follow.
Statelessness
NACL rules are stateless. This means the state of connections is not tracked, and inbound and outbound traffic is filtered separately. Return traffic is not automatically allowed just because the outbound request was allowed. Explicit rules are required for each direction of traffic.
Therefore, if you create a rule to allow traffic in one direction, you may also need a separate rule to allow the response in the opposite direction.
Default rule
Each NACL must have a default rule, which applies its action to all traffic that did not match any other rules in the list.
Best practice is to set your default rule to Deny, and use the Allow action for all other rules. This way, you have fine-grained control over the traffic allowed to flow, and all other traffic is blocked by default.
Nonetheless, you can choose to set your default rule to Allow if you wish. In this case, all other rules in the list should use the Deny action, to filter out the specific traffic you want to block. All other traffic will be permitted by the default rule.
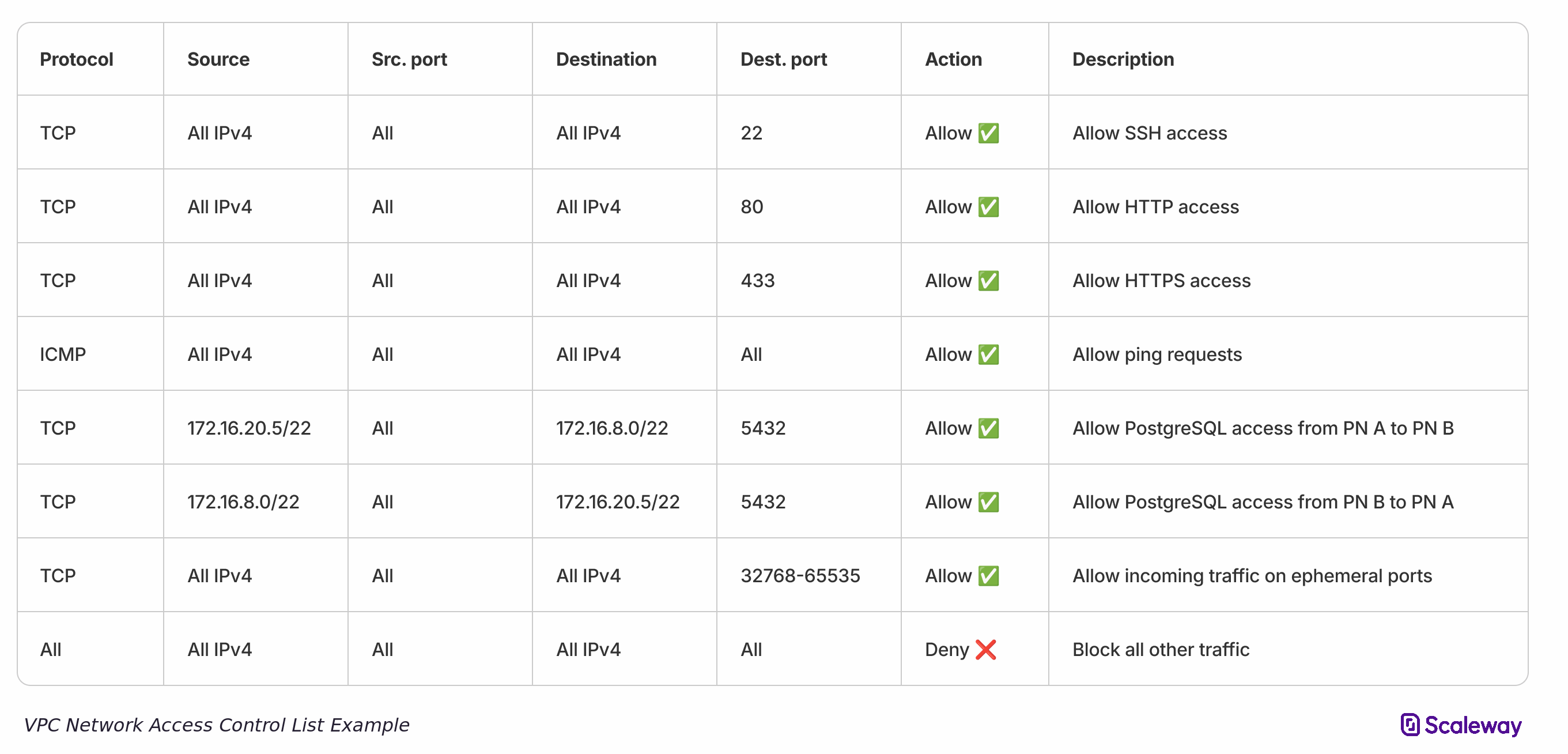
NACL example
The table below shows an example of a NACL for IPv4 traffic:
-
A number of TCP rules allow connections to the specific ports necessary for SSH, HTTP, and HTTPS traffic. These rules allow all IPv4 sources within the VPC to connect to these ports, for all IPv4 destinations.
-
An ICMP rule allows all ICMP traffic from/to all IPv4 addresses on all ports, effectively permitting all ping requests within the VPC to function.
-
A TCP rule allows PostgreSQL access on port 5432 from one Private Network (172.16.2.0.5/22) to another Private Network (172.16.8.0/22). An inverse rule also allows PostgreSQL access from Private Network B to A.
-
A TCP rule allows connections from all IPv4 sources to all IPv4 destinations on the port range
32768-65535, effectively allowing all return (incoming) traffic towards ephemeral ports. -
The default rule blocks all traffic not explicitly allowed by one of the rules above.
NACL limitations
Network ACLs cannot be used to block or filter the traffic to or from the following:
- Scaleway DNS
- Scaleway DHCP
- Scaleway Instance metadata
- Kubernetes Kapsule task metadata endpoints
- License activation for Windows installation on Elastic Metal or Instances
NACLs have the same resource limitations as VPC routing.
NACLs are currently available only via the Scaleway API and developer tools. They are not yet available in the Scaleway console.
NACL quotas
NACL quotas are as follows:
- A maximum of 255 rules for IPv4 (per VPC)
- A maximum of 255 rules for IPv6 (per VPC)